An eduroam Sunday in Canada
May 10, 2013 Leave a comment
One aspect of being the eduroam operator in Canada is how to maintain the high quality of service eduroam is known for and respond to issues that may arise before end users encounter them. To do this, CANARIE has taken a proactive stance to monitoring the health and performance characteristics of eduroam in Canada and works with domestic eduroam sites to improve the service or diagnose issues. An offshoot of this investment is being able to better understand how the service is used through the performance monitoring data and feed this information back in to improve on the eduroam environment.
This is not a small undertaking as eduroam interconnects 48 sites across Canada as well as to the international eduroam system of 60 plus countries.
What piqued our interest and this blog post is a particular Sunday in May had higher traffic than traditionally expected, much like a weekday, and we wanted to see if we could find out why. As we dug into our numbers we visualized the data in a number of dimensions, by time and by location to better depict how eduroam is being used. It shows how mobile users can be anytime and anywhere when they are connected with CANARIE and CAF.
The Stats
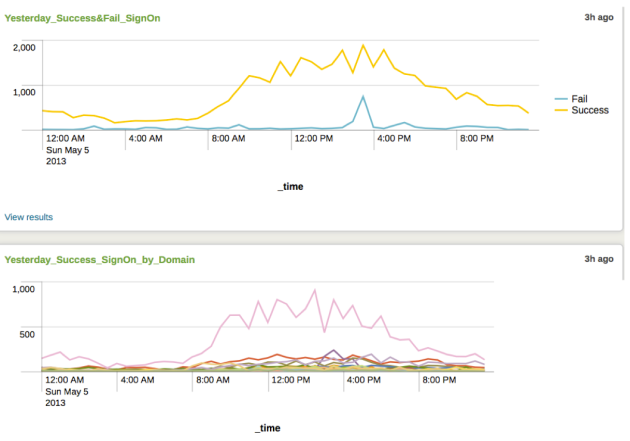
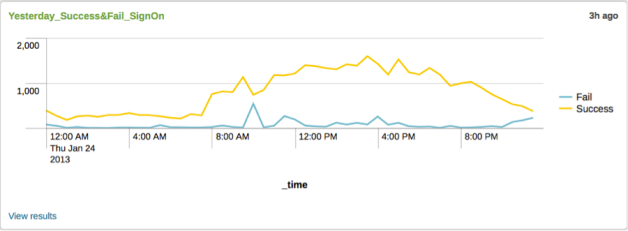
The daily report for Sunday that shows the overall hourly traffic that the Canadian eduroam servers observe. Traffic is exclusively those who are mobile and not at their home institution and are sign ons, not individual users. A sign on can be a single user, but from multiple devices or from a single device as they move around.
The graph below shows traffic across Canada on Sunday May 5th, 2013. The stats behind the line are from our sites across Canada. The Success line is self explanatory, but a ‘Fail’ entry may be due to a variety of reasons and be very intermittent as shown in the spike just before 4pm below. Being able to identify these is always a work in progress to keep the quality of service as high as possible. This one looks transient and quickly goes away.
The above graph illustrates individual traffic by domain. We have masked the domains and will focus analyzing stats for the highest line in the graph.
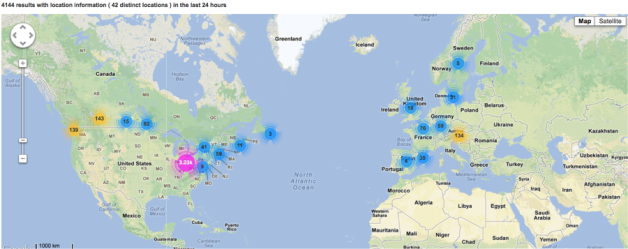
So where are Canadian mobile users benefiting from eduroam?
Short answer: All over the world!
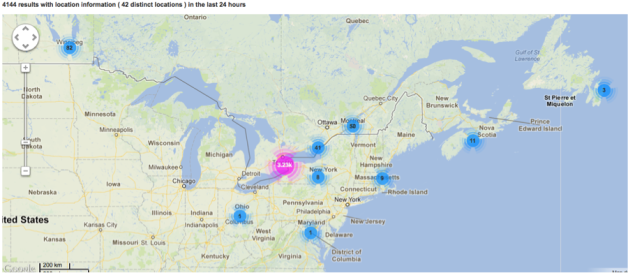
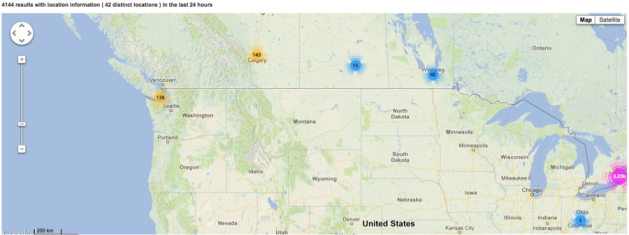
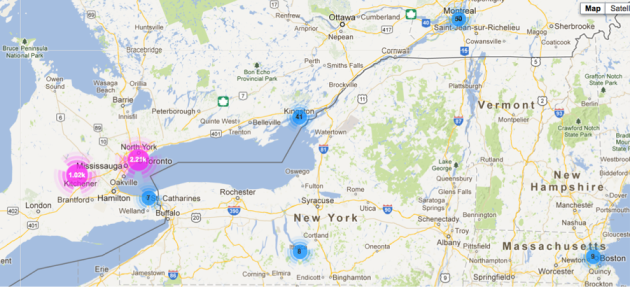
Zooming in on traffic for this one domain and overlaying it on a map we get an idea just how mobile this domain’s users are. Remember this data spans the 24hrs on Sunday.
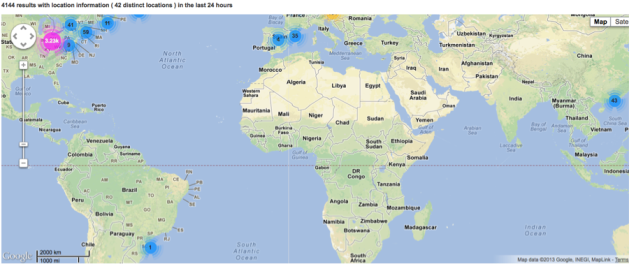
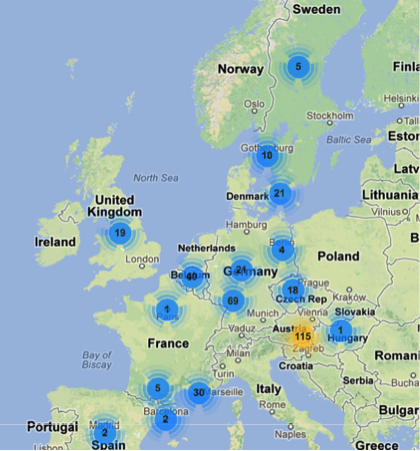
Here are a few views from other regions around the world for this domain:
Central and northern Europe:
Inside Canada
Eastern Canada and North East USA:
Western Canada
Now in the Eastern Ontario area:
Observations
All in all, very interesting just how mobile users are in this one domain. It also drives home the point that being connected is not only important across Canada, but worldwide and not just Monday to Friday 9-5 either, but 7 days a week, 24×7. You can see this in the first graph at the top of this post as the successful sign ons never goes to zero even at 4am Eastern — somewhere in the world there are people from this domain using their home institution credentials.
While obviously a great benefit for eduroam users to be on wifi around Canada and the world, behind the scenes it allows eduroam site operators to avoid issuing guest accounts and/or having to running open WiFi access points to support mobile users all the while maintaining the appropriate level of certainty of who is using their network.
I would be remiss if I did not extend the invitation to those not connected to CAF to join and expand the coverage of eduroam even further in Canada. We would love to have you connected!
Postscript
I will be presenting at CANHEIT 2013 in Ottawa on All Things Eduroam as well as our work on simplifying participating with CAF for eduroam and Federated Single Sign On(SSO) in my Leveraging the Cloud to Deliver Identity Services talk. See you there!